Unlocking the Power of Fine-Grained Password Policies in Active Directory
In the realm of network security, safeguarding user credentials is paramount. Active Directory (AD), the cornerstone of identity management in many enterprise environments, traditionally enforced a single password policy across the entire domain. However, with the advent of Fine-Grained Password Policies (FGPP), administrators can now tailor password and account lockout policies with precision, catering to the diverse security requirements of different user groups within an organization. This article delves into the intricacies of configuring FGPP in the Active Directory Administrative Center (ADAC), ensuring your network’s security posture is both robust and flexible.
Understanding Fine-Grained Password Policies
Before we embark on the configuration journey, it’s crucial to grasp what FGPP entails. FGPP allows for the creation of multiple password policies within a single domain, enabling administrators to apply different restrictions for password complexity, length, and account lockout settings to different sets of users. This is particularly useful for organizations that need to enforce stricter password rules for users with elevated privileges or access to sensitive information.
Prerequisites for FGPP Configuration
To configure FGPP, there are certain prerequisites that must be met:
- Active Directory Domain Services (AD DS) must be running at least Windows Server 2008 domain functional level.
- Access to the Active Directory Administrative Center with appropriate administrative privileges.
- A clear understanding of the user groups that require distinct password policies.
Step-by-Step Guide to Configuring FGPP
Launching Active Directory Administrative Center
Begin by accessing the ADAC. This can be done by opening the Server Manager, selecting ‘Tools’, and then clicking on ‘Active Directory Administrative Center’. Alternatively, you can run dsac.exe from the command prompt or search for ‘Active Directory Administrative Center’ in the start menu.
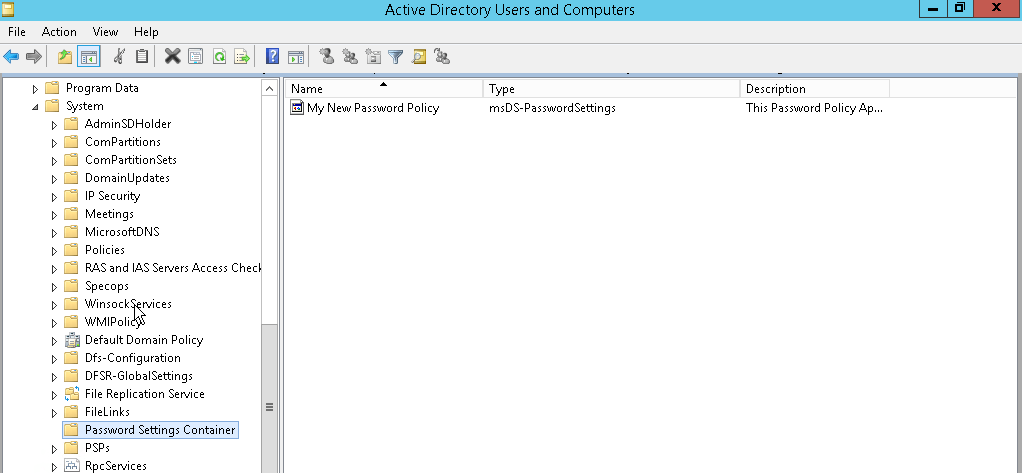
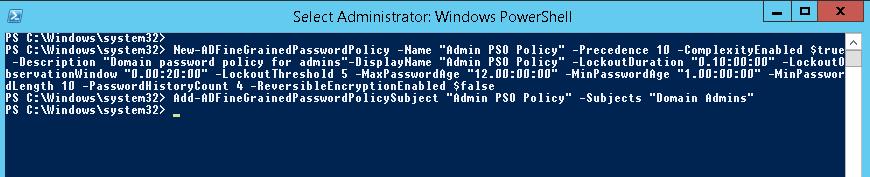
Creating a New Password Settings Object (PSO)
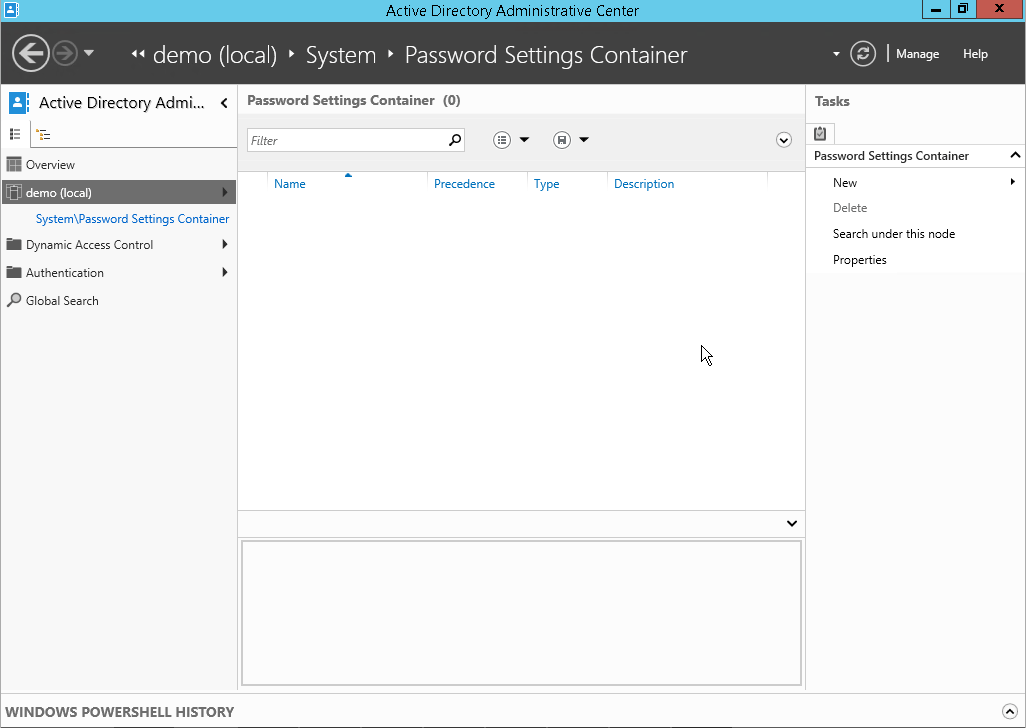
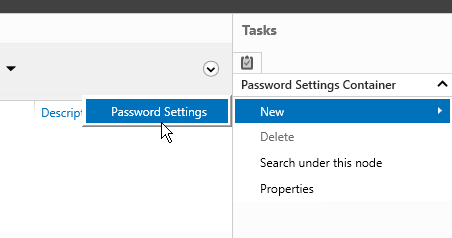
Within ADAC, navigate to the ‘System’ container and then to the ‘Password Settings Container’. Here, you will create a new PSO by right-clicking on the ‘Password Settings Container’ and selecting ‘New’ followed by ‘Password Settings’.
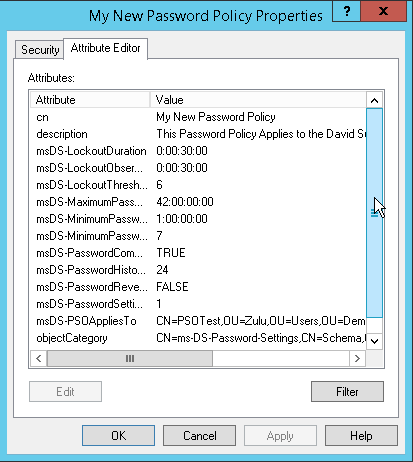
Configuring PSO Attributes
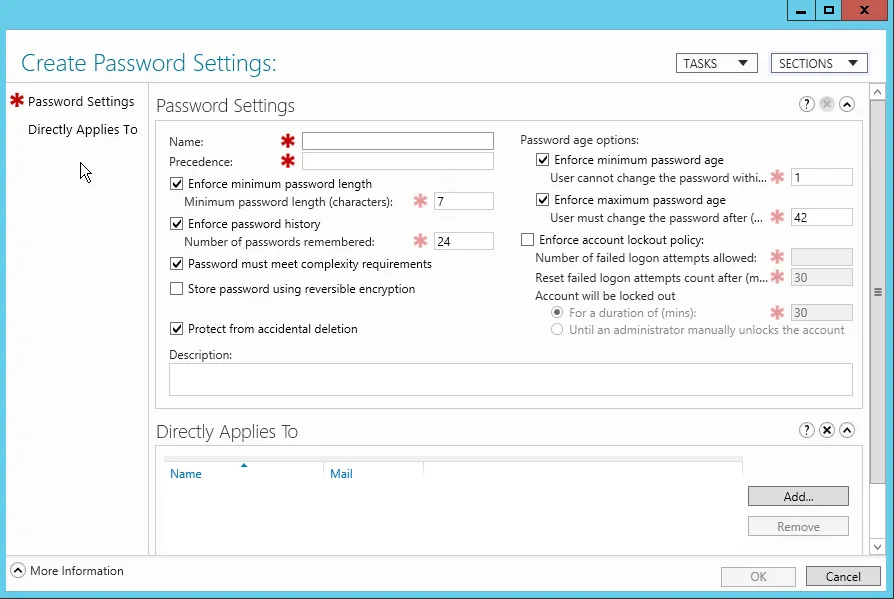
In the ‘Create Password Settings’ dialog, you’ll need to configure several attributes:
- Name: Assign a descriptive name to the PSO for easy identification.
- Precedence: Set a value that determines the PSO’s priority relative to other PSOs. Lower numbers have higher precedence.
- Password properties: Define the password complexity, history, length, and age requirements.
- Account lockout settings: Specify the number of failed login attempts that will trigger an account lockout and the duration of the lockout.
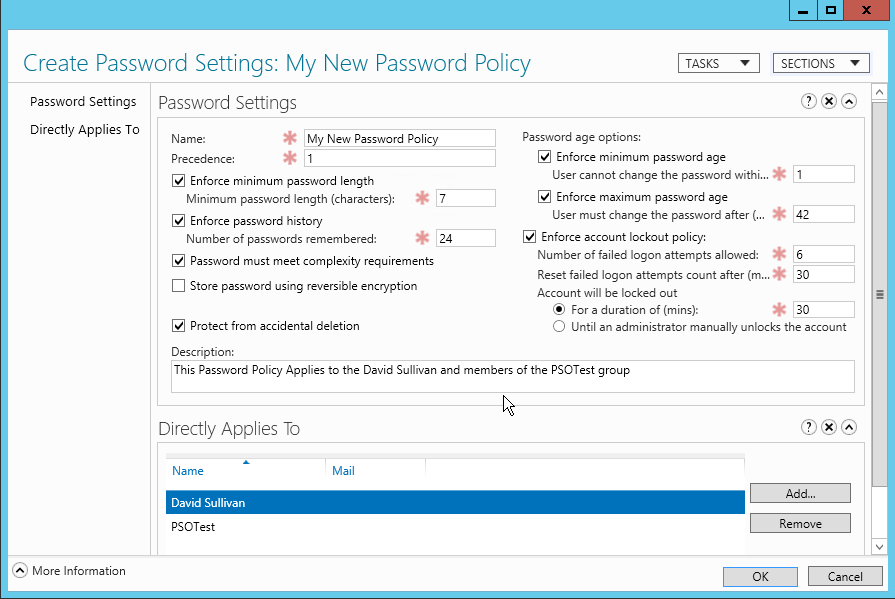
Applying the PSO to User or Group Objects
Once the PSO is configured, it needs to be applied to user or group objects. This is done by adding the user or group to the ‘Direct Applies To’ section of the PSO properties. You can apply a PSO to individual users or global security groups.
Best Practices for FGPP Implementation
When implementing FGPP, consider the following best practices:
- Use a clear naming convention for PSOs to reflect their purpose and scope.
- Set precedence values carefully to avoid conflicts between multiple PSOs.
- Regularly review and update PSOs to align with evolving security policies.
- Limit the number of PSOs to maintain manageability.
- Document all PSOs and their assigned groups for future reference.
Monitoring and Troubleshooting FGPP
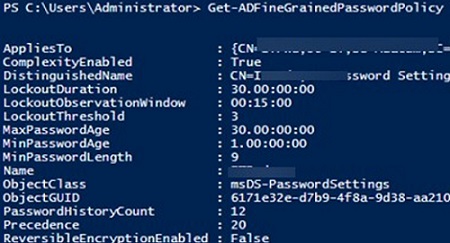
After configuring FGPP, it’s essential to monitor its impact and troubleshoot any issues that arise. Use the ‘Resultant PSO’ feature in ADAC to verify which PSO is applied to a user account. Additionally, keep an eye on security logs for account lockout events to ensure policies are not too restrictive and causing unnecessary disruptions.
Case Study: Implementing FGPP in a Financial Institution
Consider a financial institution that requires different password policies for its regular employees, IT staff, and executive team. By implementing FGPP, the institution can enforce a standard policy for most employees, a more stringent policy for IT staff who have access to critical systems, and an even stricter policy for executives who handle sensitive financial data. This targeted approach enhances security without imposing unnecessary restrictions on users who don’t require them.
FAQ Section
What is the minimum domain functional level required for FGPP?
The minimum domain functional level required for FGPP is Windows Server 2008.
Can FGPP be applied to distribution groups?
No, FGPP can only be applied to user objects or global security groups.
How do I determine which PSO is applied to a user?
Use the ‘Resultant PSO’ feature in ADAC to determine which PSO is applied to a user account.
What happens if multiple PSOs are applied to a user?
If multiple PSOs are applied to a user, the PSO with the lowest precedence value (the smallest number) takes effect.
Can I apply a PSO to an organizational unit (OU)?
No, PSOs cannot be directly applied to OUs. They must be applied to user objects or global security groups within the OU.
Conclusion
Fine-Grained Password Policies offer a powerful tool for enhancing security in Active Directory environments. By following the steps outlined in this guide and adhering to best practices, administrators can effectively configure FGPP to meet the specific security needs of different user groups. As cyber threats continue to evolve, leveraging FGPP will be crucial in maintaining a robust defense against unauthorized access and safeguarding sensitive information.
References
For further reading and a deeper understanding of FGPP and Active Directory, consider exploring the following resources:
- Microsoft’s official documentation on Active Directory Domain Services: AD DS Getting Started
- Detailed guide on Fine-Grained Password Policies: Understanding Password Policies
- Security best practices for Active Directory: AD DS Security Best Practices
